Device profiles and Alarm
1. Overview
Device Configuration allows you to set some message handling methods common to a certain class of devices, such as rule chaining, message transfer queues, transport protocol configuration, alarm rule configuration, etc.
2.Device Configuration Creation
During the device configuration creation process, you need to set the device configuration details, transmission configuration, alarm rules, and device preconfiguration respectively, and the creation process is as follows.
Device Configuration Details
In the details, you can configure the following:
Name: required field, the name of the device configuration;
Default Rule Chain: optional, you can specify which set of rule chains to use, if it is not filled, the default root rule chain is used;
Mobile Dashboard: an optional item that specifies the dashboard that is used by the mobile application as the device details;
Queue: optional, you can specify the policy for message submission and processing, the default is Main;
Default edge rule chain: no need to configure;
Device configuration image: optional, you can upload a device image;
Description: optional, device description;
Transport Configuration
In the transmission configuration, you can configure the protocol for uploading device data, and the system provides the following protocols:
Default: Support basic MQTT, HTTP and CoAP transmission, no special needs generally choose the default;
MQTT: Enable advanced MQTT transmission settings for advanced configuration;
CoAP: Enable advanced CoAP transmission settings for advanced configuration;
LWM2M: LWM2M transmission type, advanced configuration is available;
SNMP: Specify SNMP transport configuration, enabling advanced configuration;
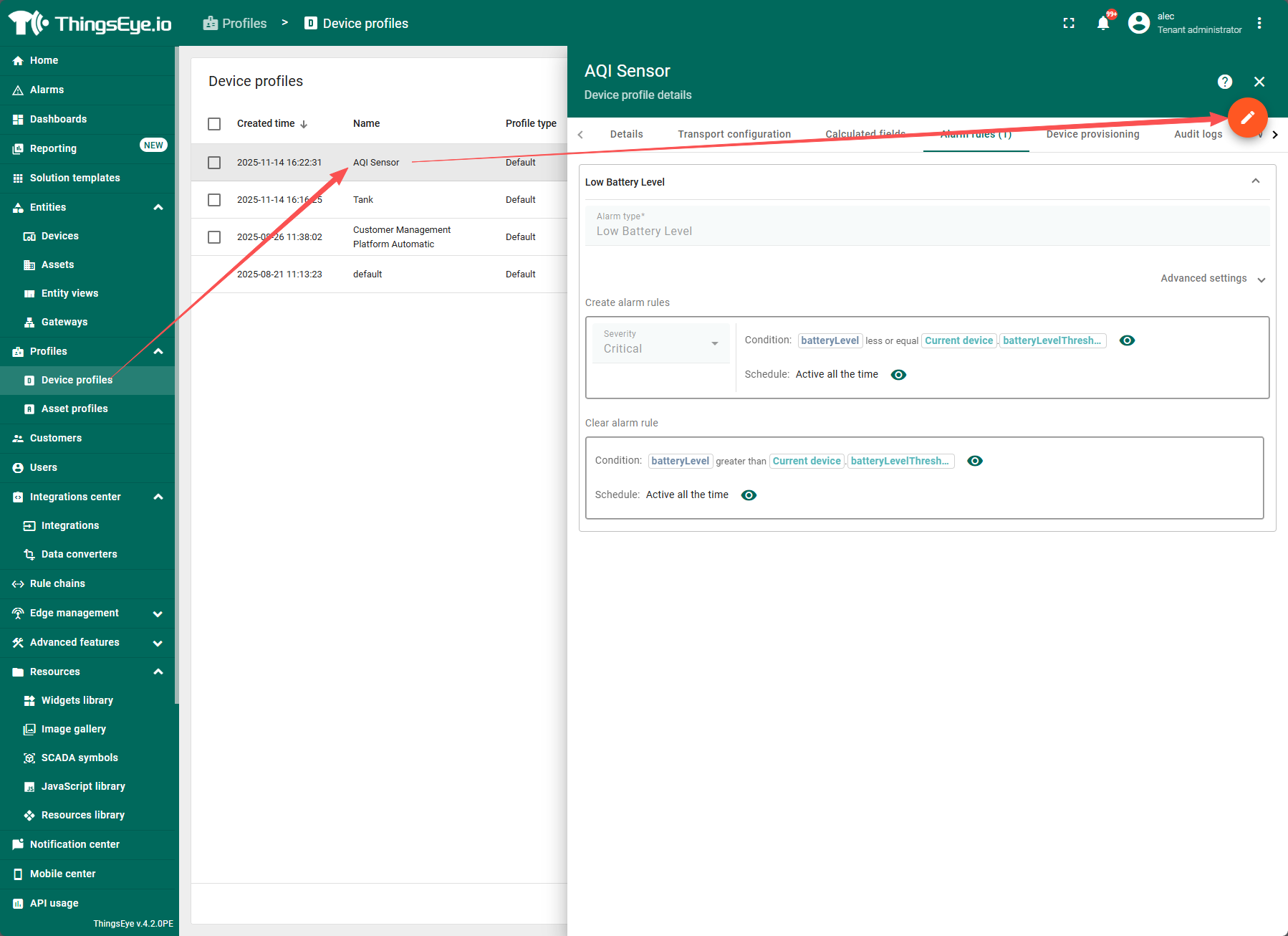
Alarm Rules
In the alarm rules configured by the device, you can configure the conditions for alarm creation and elimination (the effect is the same as that of configuring in the Rule Engine, and the configuration here can avoid coding).
Go to the Alert Rule Configuration tab and click Add Alert Rule to enter the Alert Rule Configuration page.
3.2 Creat device profiles and set up Alarm
Device configuration can set common message processing methods for a certain type of device, such as rule chain, message transmission queue, transmission protocol configuration, alarm rule configuration, etc.
3.2.1 Creat device profiles
In the process of creating device configuration, it is necessary to separately set device configuration details, transmission configuration, alarm rules, and device pre configuration. The creation process is as follows.
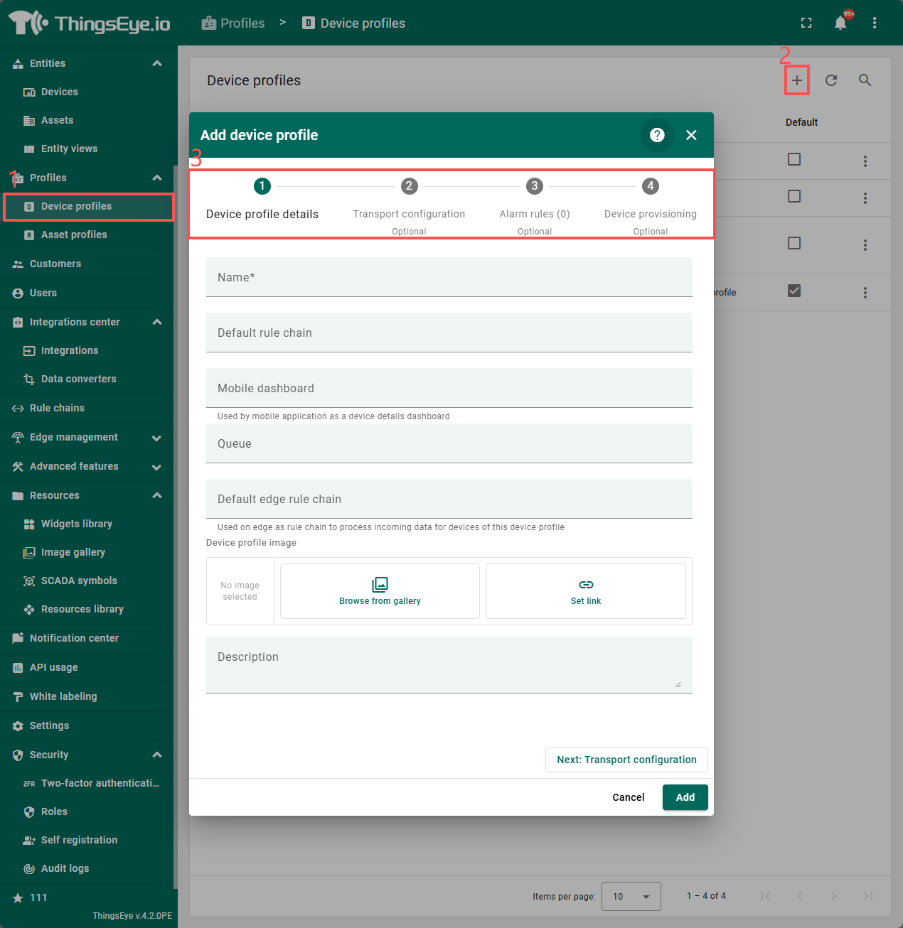
Equipment configuration details
In the details, the following configurations can be made:
Name: required field, the name of the device configuration;
Default rule chain: optional item, can specify which set of rule chains to use. If not filled in, the default root rule chain will be used;
Mobile dashboard: optional field, specifying the dashboard used by the mobile application for device details;
Queue: optional, can specify the strategy for message submission and processing, default is Main;
Default edge rule chain: No configuration required;
Equipment configuration image: optional, device images can be uploaded;
Description: Optional field, equipment description;
Transmission configuration
In the transmission configuration, the protocol for uploading device data can be configured, and the system provides the following protocols:
Default: Supports basic MQTT, HTTP, and CoAP transmission. If there are no special requirements, the default is generally selected;
MQTT: Enable advanced MQTT transport settings for advanced configuration;
CoAP: Enable advanced CoAP transmission settings for advanced configuration;
LWM2M: LWM2M transmission type, capable of advanced configuration;
SNMP: Specify SNMP transmission configuration for advanced configuration;
3.2.2 Set up Alarm
3.2.2.1 Creat alarm
In the alarm rules of device configuration, the conditions for creating and eliminating alarms can be configured (the same effect as configuring in the rule engine, where configuration can avoid encoding).
Go to the Alarm Rule Configuration tab, click Add Alarm Rule, and enter the Alarm Rule Configuration page.
Alarm creation rule configuration:Multiple items can be created using the 'Add Create Condition' button.
Severity level:The system provides five severity levels of alarms for configuration personnel to choose from, namely dangerous, important, secondary, warning, and uncertain, and can be selected according to the situation.
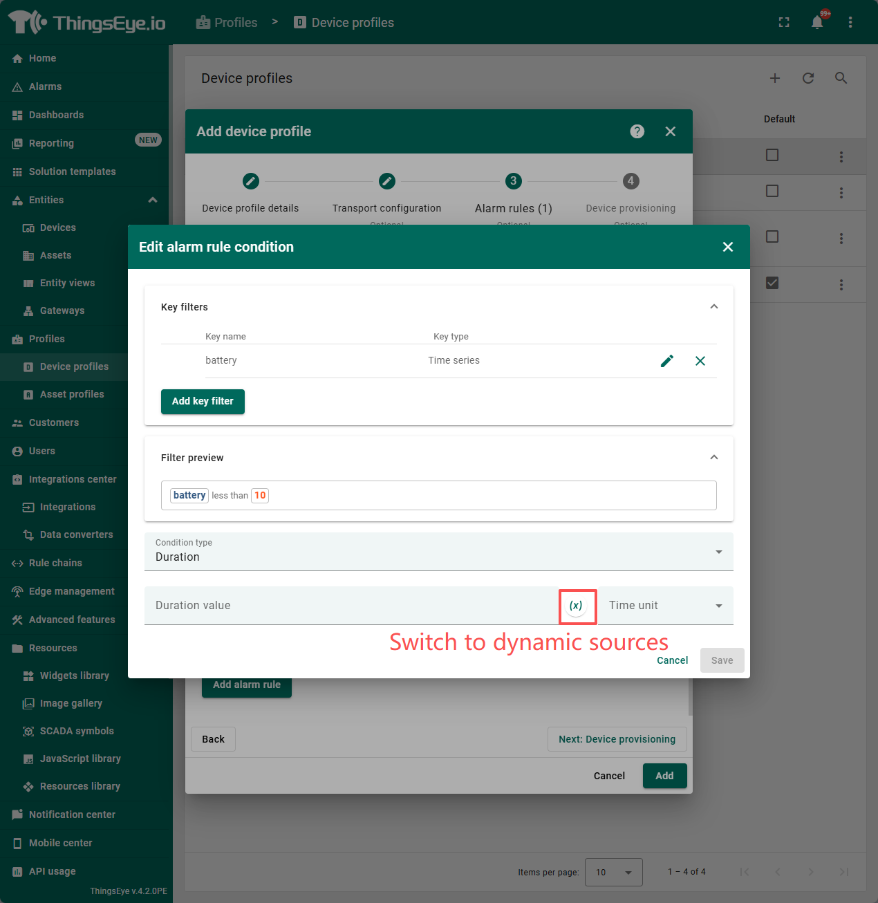
condition:The condition requires configuring the logic for creating alarms. Click the "Add Alarm Rule Condition" button and follow the steps below to complete the creation of an alarm rule condition.
step1:
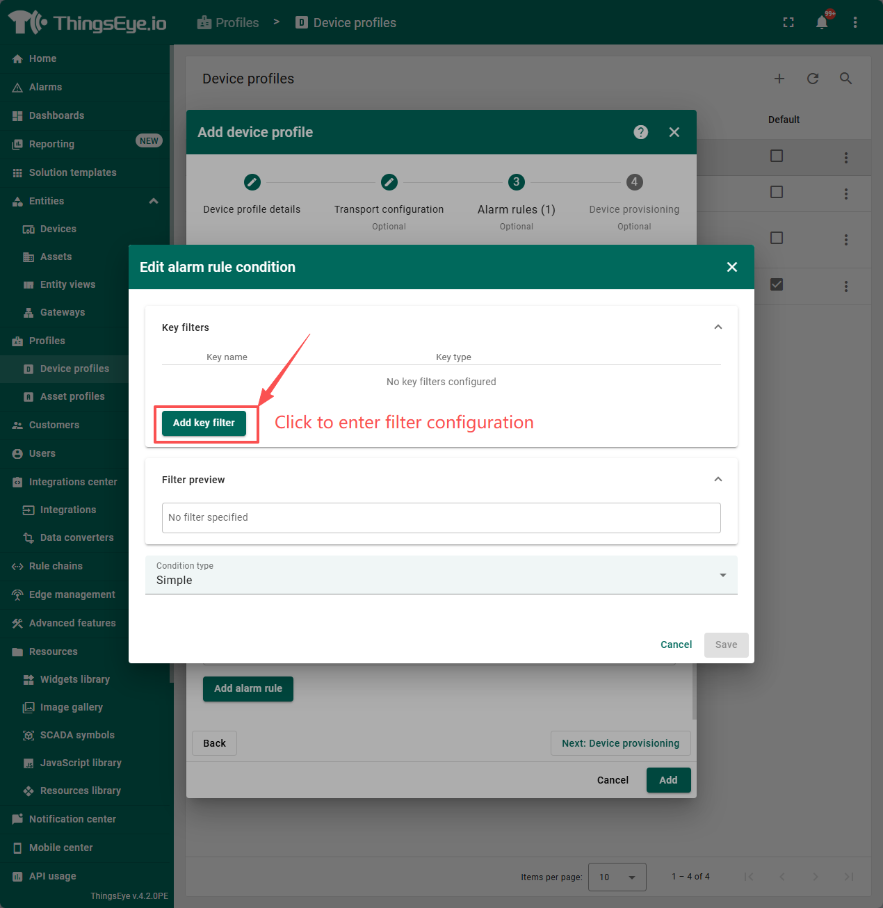
step2:
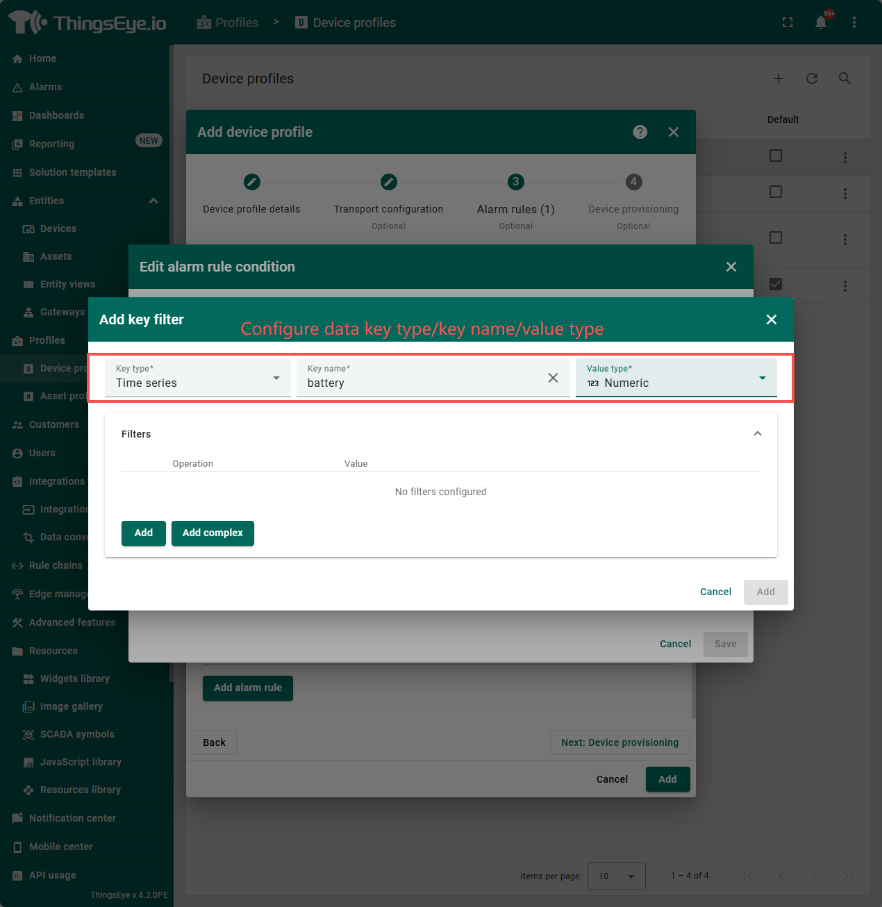
step3:
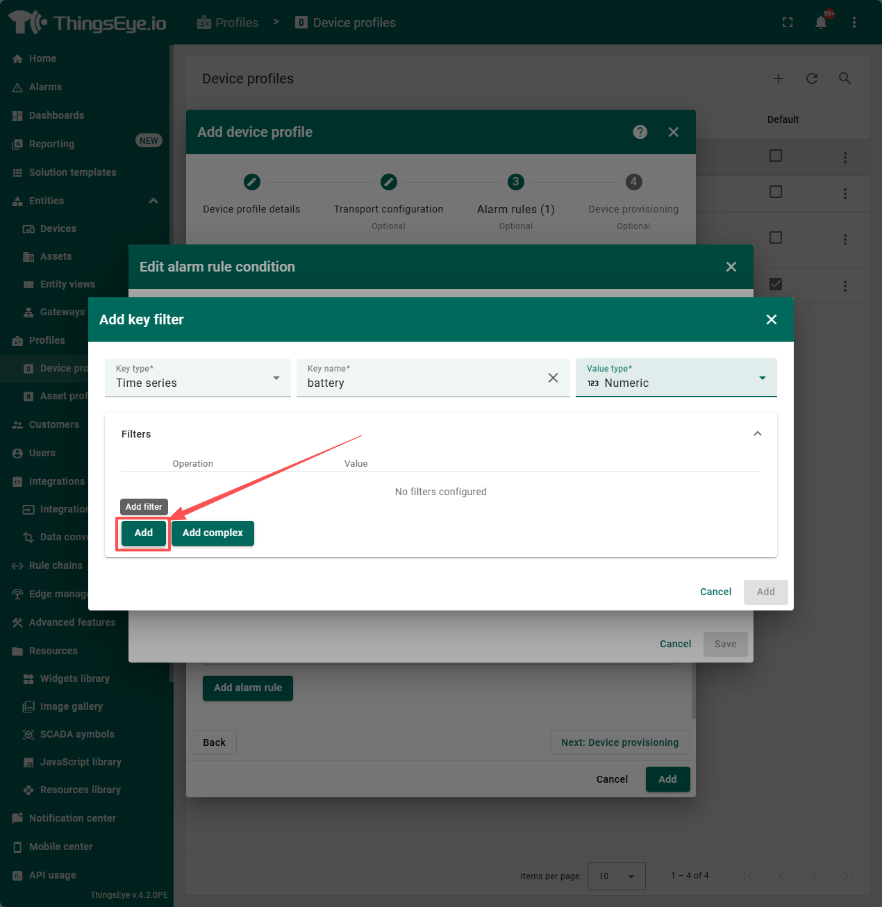
step4:
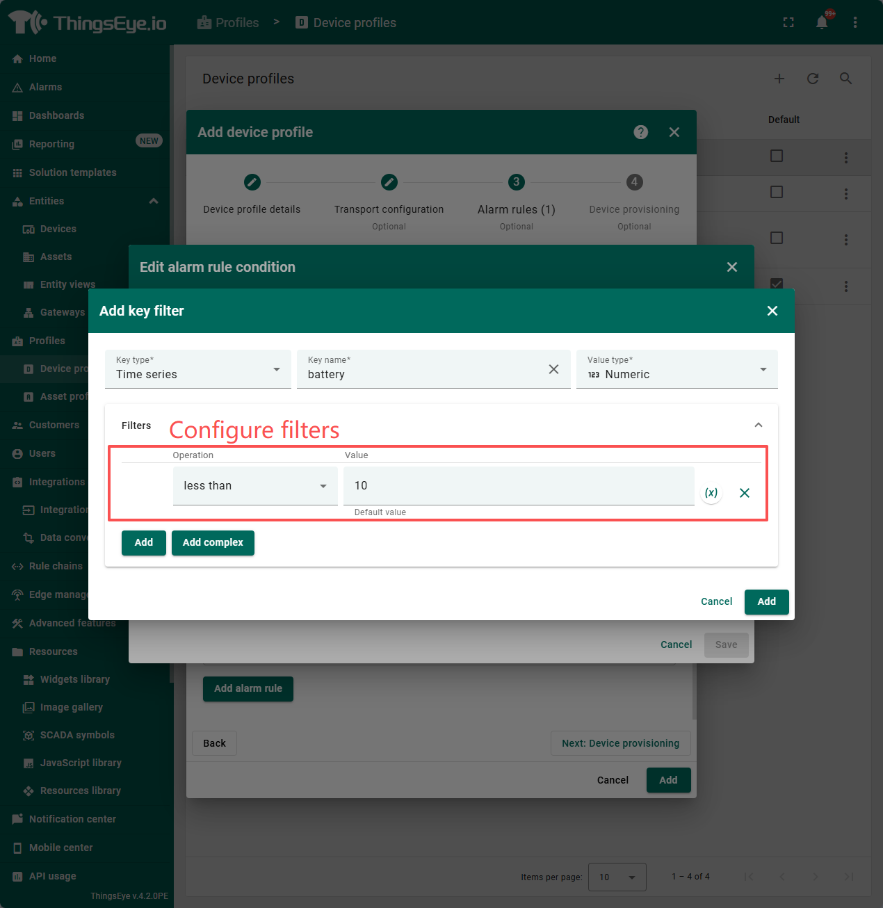
step5:
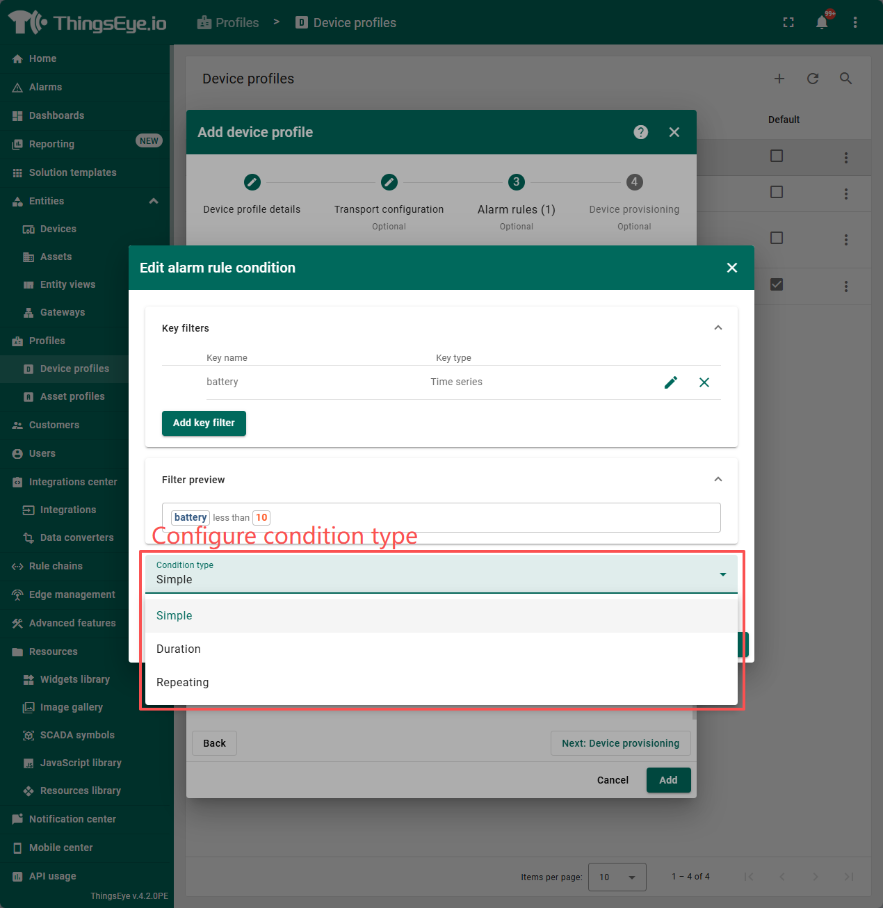
Among them:
When configuring the filter in step 2, the system provides three key types for selection, namely attribute, Timeseries, and constant. When selecting the first two, the key name is a dropdown menu, and you can choose the corresponding attribute name; When selecting a constant, the key name is an input box and you need to input it yourself. The value type is a dropdown selection box, including four types to choose from: string, number, boolean, and date time.
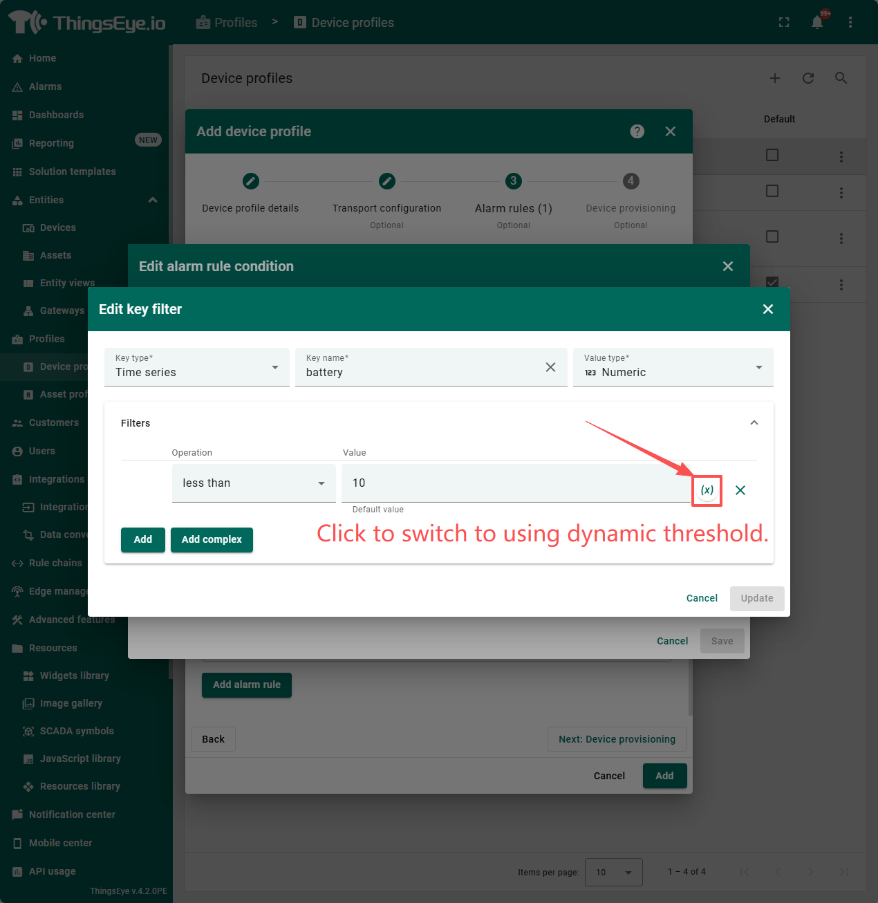
When configuring the filter in step 4, multiple logics can be added by clicking the add button; Operate as a dropdown selection box, providing various comparison logics; The value is the threshold for comparison. The dynamic comparison threshold configuration can be achieved through the following operations. Note that it is necessary to create the source attributes filled in for the selected dynamic source type in advance (the configuration method is described in https://wiki.thingseye.io/xwiki/bin/view/Main/Basic%20configuration%20of%20rule%20chains/' customer attributes and tenant attributes).

When configuring the condition type in step 5, the system provides three types: simple, duration, and repetition. When selecting the duration, it is necessary to configure the value and time unit of the duration, which can also be configured using dynamic sources; When selecting repetition, it is necessary to configure the number of repetitions, which can also be configured using dynamic sources.
3.2.2.1 clear alarm
The configuration and creation steps of alarm clearing rules are exactly the same, only the difference in configuration content is not elaborated here.
3.2.3 replace device profile